Linux Container and Docker Container
Let's Understand the Features of Linux/Docker Container.
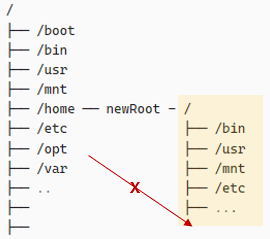
The early concept of containers in Linux(chroot).
When a specific directory path is set as the root directory using chroot, a chroot jail is created. A chroot jail refers to an environment where files and directory resources outside the chrooted root directory cannot be accessed. Because of this isolation, chroot was used to minimize data leaks and security risks.
What was the drawback of chroot? The main issue was with libraries. When a process changes its root directory using chroot, the libraries it previously referenced may reside in the parent directory of the new root directory, making them inaccessible.
LXC(LinuX Container)
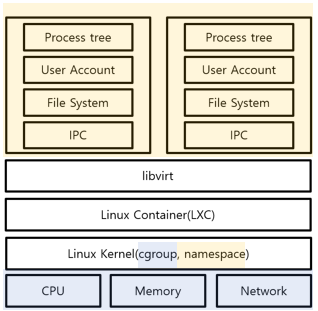
Linux Containers(LXC) were developed to overcome the limitations of chroot. When thinking of virtualization technology, one might consider Virtual Machines, but unlike Virtual Machines, LXC does not virtualize the operating system itself. Instead, it utilizes the host OS as it is.
LXC isolates elements such as the process tree, user accounts, file system, and IPC for each container, creating a virtual space separate from the host. It also allocates resources like CPU, memory, and network to each container. In this context, libvirt is a collection of APIs, daemons, and management tools that support virtualization in Linux.
In the Linux kernel, cgroups(Control Groups) provide a virtualized space where resources such as CPU, memory, storage, and network can be allocated. Additionally, namespaces(Namespace isolation) isolate elements such as the process tree, user accounts, file system, and IPC, creating a fully isolated environment from the host OS.
- cgroups: Provides a virtualized space where CPU, memory, disk, and network resources are allocated.
- namespace: Separates the file system, user accounts, and other system components from the host OS (the OS installed on the hardware).
LXC enhances chroot by leveraging these system-level virtualization technologies.
Docker Container
As mentioned earlier, while LXC provided an isolated environment, it lacked essential features for effectively running services within it. Docker, built on cgroups and namespaces, extends these capabilities by offering functionalities such as image and container management, making it more practical for real-world use.
Like LXC, Docker runs multiple containers on a single OS. Therefore, there is no need to install a guest OS for each process (as in Virtual Machines), and the system call process for accessing hardware resources is relatively simple. Since Docker provides a lightweight virtualization technology compared to traditional virtualization, it is highly scalable. Users can create containers as needed and easily remove them when they are no longer required.
While Docker shares similarities with LXC, there are clear differences. The table below summarizes these distinctions.
| Category | LXC | Docker |
|---|---|---|
| Isolation Level | Provides a full OS environment similar to a VM | Isolates at the application level |
| Kernel Sharing | Shares the host OS kernel | Shares the host OS kernel (optimized for running containerized applications) |
| File System | Provides a complete root file system (including /bin, /lib, /etc) | Uses a layered file system (OverlayFS) for lightweight operation(/var/lib/docker/overlay2) |
| Networking | Supports a separate network stack (can assign a physical interface) | Uses NAT-based networking by default |
| Process Management | Can run multiple processes similar to the host OS | Typically runs a single main process inside the container |
| Advantages | High flexibility, provides a full OS environment | Lightweight, fast deployment, portability |
| Disadvantages | Relatively heavy, requires VM-like configuration | Limited OS environment, single-process execution model |
 Docker containers(Source: Docker Homepage)
Docker containers(Source: Docker Homepage)